Imagine this: you’re a graphic designer, meticulously crafting a vibrant logo for a client. You’ve painstakingly selected the perfect colors, ensuring they perfectly reflect the brand’s identity. You’re about to finalize the design, but then… you’re met with an error message: “Authentication required to create a color profile.” Frustration washes over you as you realize your creative flow is halted due to a security measure you haven’t encountered before. This scenario highlights the growing importance of authentication in the world of color management, a vital aspect of ensuring consistent and accurate color reproduction across different devices and workflows.
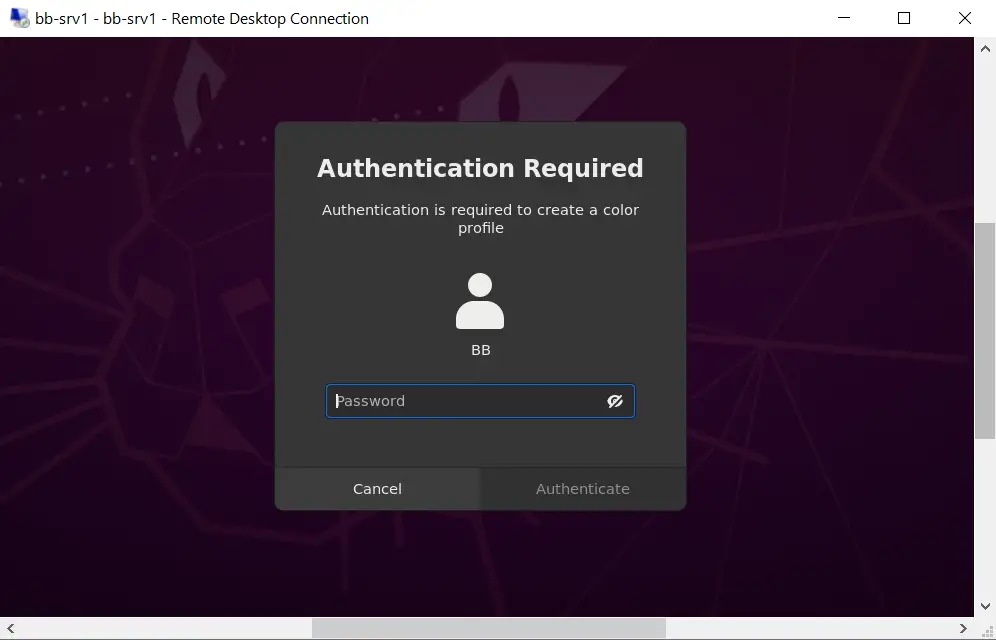
Image: devanswe.rs
But why is authentication necessary for creating color profiles? What are the benefits and challenges associated with this security measure? This article will delve into the reasons behind this growing trend, exploring the intricacies of color profile creation and its relationship to authentication.
The Importance of Color Profiles: A Foundation for Accurate Color Reproduction
Color profiles are digital files that act as a bridge between devices and applications, ensuring that colors are displayed and printed accurately. They contain information about how a specific device perceives and reproduces colors, enabling consistent color representation across various platforms. Without color profiles, the same color can appear drastically different on different screens or printers, leading to inconsistencies in design and printing.
Imagine creating a stunning website with vibrant hues only to discover that the colors appear dull and washed out on a different monitor. This is a common issue without proper color management and highlights the crucial importance of accurate color profiles. They act as a common language, translating color information so that it is interpreted correctly regardless of the device.
Why Authentication is Required: Safeguarding Color Profiles and Ensuring Trust
The Need for Security: Protecting Valuable Color Data
The rise of authentication requirements for creating color profiles is a direct response to the increasing need for security in the digital world. Color profiles contain valuable information about a device’s color capabilities, and their misuse can lead to several issues, including:
- Color manipulation: Unauthorized access to color profiles could allow individuals to manipulate colors, altering the intended shade for fraudulent purposes or personal gain.
- Data breaches: Color profiles could be vulnerable to data breaches, exposing sensitive information about a device’s color characteristics to unauthorized entities.
- Compromised workflows: Tampering with color profiles can disrupt creative workflows by introducing inconsistencies and errors, leading to time-consuming corrections and rework.

Image: www.slideshare.net
Building Trust: Ensuring Data Integrity and Origin
Authentication plays a crucial role in building trust within the color management ecosystem. When a color profile is created with authentication, it signifies that the data is legitimate and has not been tampered with, providing peace of mind for designers, printers, and other professionals who rely on accurate color reproduction. This trust is built upon a system of verification and validation, ensuring that the color profile is genuine and originates from a reliable source.
Maintaining Consistency and Accuracy: Protecting the Value of Creative Content
Authentication also safeguards the integrity of color profiles, preventing unauthorized modifications or deletions that could compromise their accuracy. By ensuring that only authorized users can create and edit profiles, authentication safeguards the data’s integrity, maintaining color consistency throughout the creative process.
Latest Trends in Color Profile Authentication
The field of color profile authentication is constantly evolving, with new technologies and approaches emerging to enhance security and user experience. Some of the latest trends include:
- Cloud-based authentication: Storing and managing color profiles in secure cloud platforms offers a convenient and robust method for authentication, enabling centralized access and control.
- Digital signatures: Using digital signatures to verify the authenticity of color profiles provides a high level of assurance, ensuring the integrity of the data and preventing unauthorized modifications.
- Two-factor authentication: Implementing two-factor authentication strengthens security by requiring users to provide multiple forms of identification, reducing the risk of unauthorized access.
As the use of color profiles continues to grow, the importance of robust authentication measures will only become more apparent. These technologies are not only crucial for protecting sensitive information but also play a vital role in maintaining the trustworthiness and integrity of the color management ecosystem, ensuring that creative professionals can rely on accurate color reproduction throughout their workflows.
Tips for Managing Color Profiles with Authentication
While authentication adds a necessary layer of security, it’s essential to understand how to navigate it effectively to minimize disruptions in your workflow. Here are some tips for managing color profiles with authentication:
- Choose reputable vendors: Opt for color profile creation tools and services from reputable vendors that prioritize security and adhere to industry best practices.
- Strong passwords: Use strong, unique passwords for your color management accounts and avoid sharing them with others.
- Regular updates: Keep your color management software and applications up-to-date with the latest security patches to mitigate potential vulnerabilities.
- Backups: Regularly back up your color profiles to ensure you have access to them even if your primary source is compromised.
- Protect your devices: Implement strong security measures for your computer systems and devices, including antivirus software and firewalls, to safeguard against malware and unauthorized access.
By following these tips, you can enjoy the benefits of secure color profile management while maintaining a smooth workflow. Remember that security is an ongoing process that requires vigilance and proactive measures to protect your valuable color data and workflows.
FAQ: Authentication and Color Profiles
Q: Why are color profiles increasingly requiring authentication?
A: The rising need for security in the digital world has driven the adoption of authentication measures for color profile creation. This is due to the valuable information contained within color profiles and the potential risks posed by unauthorized access or manipulation.
Q: What steps can I take to minimize the impact of authentication on my workflow?
A: Choose reputable color profile creation tools, use strong passwords, keep your software updated, regularly back up your profiles, and protect your devices with robust security measures.
Q: What are some of the latest trends in color profile authentication?
A: Cloud-based authentication, digital signatures, and two-factor authentication are becoming increasingly popular, offering enhanced security and user experience.
Authentication Is Required To Create A Color Profile
Conclusion
The implementation of authentication measures for creating color profiles is a crucial step towards ensuring the security, integrity, and trustworthiness of the color management ecosystem. While it may introduce new challenges, the benefits of safeguarding valuable color data and maintaining workflow efficiency far outweigh the potential drawbacks. By understanding the reasons behind authentication and implementing best practices for secure management, professionals can confidently embrace the future of color management, where accuracy, consistency, and trust are paramount.
Are you interested in learning more about color profile authentication and its impact on your creative workflow? Share your thoughts and questions in the comments below!






